If you are wondering how to prevent RDP brute force attacks efficiently, you are in the right place. The benefits of detecting how to stop RDP brute force attacks help many organizations or companies in all scales in many different ways.
Nowadays, the impact of the coronavirus pandemic drives most businesses to remote working. This big change leads to the increasing use of remote desktop applications and VPN for enterprise resources inside the corporate network. According to RDP continuous access, we need a strong RDP guard to block the ways for cyberattacks.
As RDP compromises are the most popular attack vector by far, so what would be better than learning good cybersecurity habits to avoid such dangerous attacks. This blog offers useful ways to minimize the effects of RDP brute attacks on RDP connections.
What Is a Brute Force Attack?
RDP brute force attacks are widely common in enterprise environments due to more open RDP ports. Hackers attempt to penetrate Windows systems and run malware through automating brute-force tools by a dictionary attack.
Network scanners use particular apps to enter multiple different usernames or passwords by a dictionary of a wide range of words or phrases. So, computer systems with weak credentials are easy baits to get into their RDP security.
The majority of cyber attackers take place in brute force attacks use bots to ease their bidding. During this time, server performance may take a hit as the attacks consume system resources.
Also Read: Prevent brute force attacks in 5 steps
What are the aims of RDP brute force attacks?
Hackers are interested in gaining access to your system resources and unlocking the administrator password to reach their target purpose, including disabling antivirus software, running malware, stealing valuable data, encrypting high priority files, etc.
All these actions are executed by ransomware, a type of malware that spreads through your network to take the authority of all resources. As a result, this level of disruption can significantly impact a company’s reputation, authority, identity, finances, and daily operations.
 Need a Remote Desktop?
Need a Remote Desktop?
Reliable, high-performance RDP servers with 99.95 uptime. Take your desktop on the go to all the major cities in the US, Europe, and Asia.
Get an RDP Server9 practical ways to prevent RDP brute force attacks
To easily prevent RDP brute force attacks, here are seven practical ways to configure your RDP connections more securely.
1- Come up with a secure and complex password policy
Increase password length and complexity is the first step to prevent targeted ransomware operations. Using a lengthy, strong password policy like a combination of long phrases, numbers, small and capital words, and symbols in passwords can make the best password policy for all accounts to prevent RDP password brute-force attacks.
2- Limit the RDP login access
RDP login access restriction can cut down the RDP brute force ransomware when you allow a specific number of users to access an organization’s server via RDP port directly over the internet.
Also Read: PCoIP vs RDP: Which one is better for Remote Desktop connection?
3- Benefit from multi-level authentication
Multi-factor authentication is the third highly essential method for RDP brute force protection. It uses two or more particular methods to verify user authenticity; fingertips, voice biometrics, SMs verification codes, and facial recognition are the best examples of this type of authentication.
This multi-factor authentication is a kind of advanced authentication that makes a deep security layer to deliver the right and unhacked username and password authentication method.
4- Buy RDP VPS
A reliable RDP VPS server gives you full admin access with secure connections when security and accessibility are the most critical factors for a large community of people as a challenge.
Regarding this, we suggest RDP access to authorize users to stop the risk of unauthorized gaining access to your VPS. RDP is one of the most effective methods for achieving high-performance server solutions that fulfill your remote desktop needs and control user access.
Read More: Top RDP Provider 2022
5- Maximize the computer security level
The different things that can affect your computer security are to follow these essential tips.
-
Enable Windows firewall
You need to turn on or set up a new rule for your Windows firewall to protect your computer from outgoing connections. Doing this in a firewall will block network-based threats to your local machines. -
Update your computer and other software
Keeping your computer and other software softly is highly recommended by updating the process to avoid viruses and malware. Since hackers always attempt to detect watering holes to attack your system.
-
Use antivirus software
With the help of antivirus programs or software, you can achieve excellent computer protection against hackers. Take seriously, establishing RDP connections without having antivirus software installed can harm your system. -
Lockdown any insecure and out of date computers
It is really thoughtful of you to isolate or replace the old pcs from your network as they are a security risk.
Old hardware can cause vulnerabilities to rise RDP brute attacks, and outdated computers can lead to weak aspects for hackers to exploit in your network security.
6- Use CAPTCHA code
CapTCHA codes are another valuable point to build trust in your system security. So when automated bots aim to get into your system, this strategy can deactivate brute force attacks because CAPTCHA benefits from a difficult combination of password patterns.
7- Follow endpoint security solutions
Endpoint refers to the collection of devices and systems that exists in your organization’s internal network. Endpoint security is the impactful solution to prevent types of viruses and cyberattacks on your network endpoints.
Rich endpoint security provides monitoring of all network connections and can isolate threats without business operations disruption. Avast, ESET protection, Panda Watch Guard endpoint are the best examples.
Also Read: [Fixed] RDP an Internal Error has occurred?
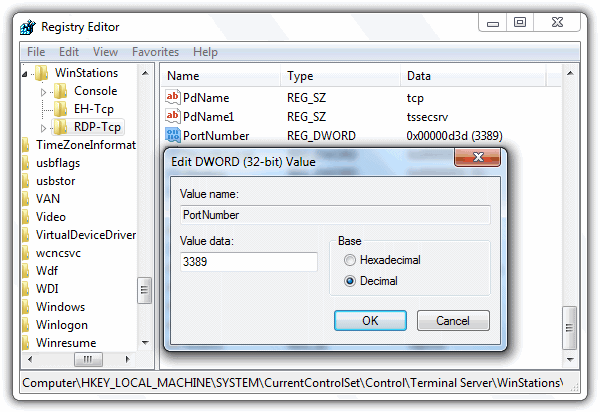
8- Change the listening port for RDP
One of the most practical and easiest ways to break into the RDP brute attacks is to change the remote desktop port. This security reason is crucial to decrease the major risk of being accessible in the port scanning process and enhance the network security to defend against RDP port 3389.
Also Read: Open Task Manager in Remote Desktop
9- Account lockout policy
Setting up the account lockout policy is the last recommended way to maintain secure network communication and lock invalid thousands of login attempts.
- Go to the Start Menu
- Type Administrative Tools
- open the program listed under ‘Best Match.’
- A window opens; double-click on Local Security Policy to open
- On the left-hand side, open to Account Policies > Account Lockout Policy
- Select the policy you need to edit
- Set a new value
- Click OK
-
Make backup copies of critical data
You have to make a backup plan in advance as an effective strategy to know the programs and products location of the backups.
 Need a Remote Desktop?
Need a Remote Desktop?
Reliable, high-performance RDP servers with 99.95 uptime. Take your desktop on the go to all the major cities in the US, Europe, and Asia.
Get an RDP ServerConclusion
That was it for the 8 practical tips to prevent RDP brute force attacks as well as possible. How to secure RDP attacks are one of the main reasons that immune the targeted ransomware.
Knowing them should undoubtedly persuade you to increase your network security level’s effectiveness and further control a computer system safely remotely.
Remember leaving RDP ports open is known as a security issue, and these useful ways are precisely the preparations that make an attacker with RDP access so dangerous.
FAQ
What is RDP and how does it work?
Remote Desktop Protocol (RDP) is a network communication protocol that provides you with access to a Windows computer remotely. An RDP broadcasts an output device like a monitor to a client, and the client interacts with the remote desktop through an input device like a mouse with the server.
What is the RDP brute force attack?
A cracker can access your RDP account through brute force guessing. As the name implies, the cracker runs a program that tries out various passwords until it gets it, and that’s the most common way they can break into your RDP.
How to prevent RDP brute force attacks?
Some of the good ways to stop RDP brute force attacks are using a strong password, RDP VPS, limit the number of logins, implement captcha, and multi-factor authentication (MFA).
Can ransomware go through an RDP?
An RDP brute force ransomware is when your RDP connection is exposed throughout the internet, and the attacker blocks you from accessing your data, usually by encrypting it and forcing you to pay for it.
What is the RDP brute force protection?
RDP brute force protection covers methods to prevent RDP password brute-force attacks by means of restricting the RDP login access, using multi-factor authentication (MFA), changing the RDP port, taking advantage of lockout policy, and especially securing your RDP via VPS. Furthermore, you can benefit from setting up a captcha, antivirus, and firewall to protect your RDP.












Usually choosing a strong and complex password does the job
If you use a secure RDP connection and do all the things in this article you should be good to go
Is using RDP on a VPS more secure than a local system RDP connection
How much does using a reliable VPS provider affect on my security? Or it does not have anything to do with the provider?
Thanks for the great article, I found what I was looking for